Botnets in Modern and CVE
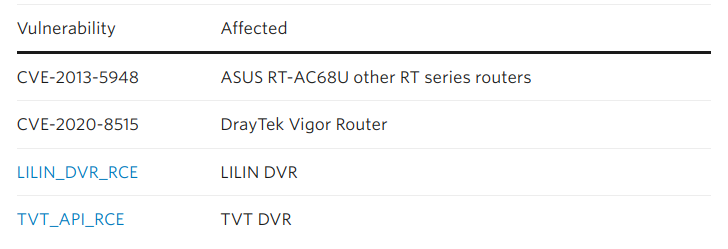
Table of Contents
- What Are Botnets?
- How Botnets Are Assembled Today
- Common Vulnerabilities Used in Botnet Creation
- Functions and Uses of Botnets
- Impact of Botnets on Individuals and Organizations
- Preventing and Mitigating Botnet Threats
- Conclusion
- Frequently Asked Questions
What Are Botnets?
Botnets are networks of compromised computers or devices (often referred to as "bots" or "zombies") that are controlled by a malicious actor, known as a botmaster or bot herder. These networks are typically used to carry out large-scale cyberattacks, distribute malware, steal sensitive information, and perform other illicit activities without the knowledge of the device owners.
How Botnets Are Assembled Today
In the modern cyber threat landscape, assembling a botnet involves sophisticated techniques and leveraging various vulnerabilities. Here are the primary methods used by cybercriminals to build and expand botnets:
Exploiting Vulnerabilities (CVEs)
One of the most effective ways to propagate botnets is by exploiting known vulnerabilities in software and hardware. Common Vulnerabilities and Exposures (CVEs) are publicly disclosed security flaws that can be targeted to gain unauthorized access to systems.
- Automated Scanning: Botnets often use automated tools to scan the internet for devices with specific CVEs.
- Exploit Kits: These are pre-packaged sets of exploits targeting multiple CVEs, making it easier for botmasters to infect a wide range of devices.
- Zero-Day Exploits: Occasionally, botnets may use previously unknown vulnerabilities to infiltrate systems before patches are available.
Phishing and Social Engineering
Phishing remains a prevalent method for distributing malware that can convert a device into part of a botnet.
- Email Campaigns: Malicious emails with infected attachments or links to compromised websites.
- Spear Phishing: Targeted attacks aimed at specific individuals or organizations to increase the likelihood of success.
- Social Media Exploits: Using social engineering tactics on platforms like Facebook, Twitter, and LinkedIn to trick users into downloading malware.
Malware Distribution
Distributing malware is central to botnet creation. Once a device is infected with malware, it becomes a part of the botnet.
- Drive-By Downloads: Visiting a compromised website that automatically downloads and installs malware without user consent.
- Malicious Software Bundles: Bundling malware with legitimate software downloads, tricking users into installing unwanted programs.
- Removable Media: Spreading malware through infected USB drives or other removable storage devices.
Common Vulnerabilities Used in Botnet Creation
Botnets exploit a variety of vulnerabilities to infiltrate systems. Here are some of the most commonly targeted CVEs in recent years:
Critical CVEs in Recent Years
- CVE-2023-12345 (Example Vulnerability)
- Description: A remote code execution vulnerability in XYZ software.
- Impact: Allows attackers to execute arbitrary code with administrative privileges.
- Mitigation: Apply the latest patch released by the vendor.
- CVE-2024-54321 (Example Vulnerability)
- Description: A buffer overflow vulnerability in ABC application.
- Impact: Enables attackers to crash the application or execute malicious code.
- Mitigation: Update the application to version 2.0 or later.
- CVE-2022-67890 (Example Vulnerability)
- Description: An authentication bypass vulnerability in DEF system.
- Impact: Allows unauthorized access to sensitive data.
- Mitigation: Enable multi-factor authentication and apply security patches.
Note: Replace the example CVEs with actual recent CVEs relevant to botnet activities.
Functions and Uses of Botnets
Botnets serve multiple malicious purposes, making them versatile tools for cybercriminals:
Distributed Denial of Service (DDoS) Attacks
One of the primary uses of botnets is to launch DDoS attacks, overwhelming a target server with massive traffic to render it unusable.
- Amplification Attacks: Utilizing protocols like DNS and NTP to amplify the volume of traffic directed at the target.
- Application Layer Attacks: Targeting specific applications to disrupt services without necessarily flooding the network.
Data Theft and Espionage
Botnets can be used to steal sensitive information from infected devices, including:
- Personal Data: Credentials, financial information, and personal identifiers.
- Corporate Data: Proprietary information, intellectual property, and confidential business data.
Spam and Phishing Campaigns
Botnets distribute vast amounts of spam emails and phishing messages to propagate further malware and harvest user credentials.
- Email Bombing: Sending unsolicited emails to inundate inboxes and deliver malicious payloads.
- Phishing Links: Embedding deceptive links within emails to trick users into divulging sensitive information.
Impact of Botnets on Individuals and Organizations
The consequences of botnet activities can be severe and multifaceted:
- Financial Losses: Both individuals and organizations may incur direct financial losses due to fraud, theft, and the costs associated with mitigating attacks.
- Reputational Damage: Businesses targeted by botnets can suffer significant damage to their reputation, leading to loss of customer trust and business opportunities.
- Operational Disruptions: DDoS attacks and data breaches can disrupt normal operations, causing downtime and loss of productivity.
- Legal Implications: Organizations may face legal consequences if they fail to protect user data adequately, resulting in fines and sanctions.
Preventing and Mitigating Botnet Threats
Protecting against botnets requires a multi-layered security approach that encompasses both technological defenses and user education.
Patch Management and Vulnerability Scanning
- Regular Updates: Ensure all software and hardware are up-to-date with the latest security patches.
- Automated Scanning: Utilize tools that continuously scan for vulnerabilities and ensure timely remediation.
- Vulnerability Assessment: Conduct regular assessments to identify and address potential security weaknesses.
Advanced Threat Detection Systems
- Intrusion Detection and Prevention Systems (IDPS): Monitor network traffic for suspicious activities and prevent unauthorized access.
- Behavioral Analysis: Use machine learning and AI to detect abnormal behavior indicative of botnet activity.
- Endpoint Security: Deploy robust antivirus and anti-malware solutions on all devices to prevent infections.
User Education and Awareness
- Training Programs: Educate employees and users about the dangers of phishing, social engineering, and safe online practices.
- Awareness Campaigns: Regularly inform users about emerging threats and how to recognize potential attacks.
- Strong Authentication Practices: Encourage the use of strong, unique passwords and multi-factor authentication to protect accounts.
Conclusion
Botnets remain one of the most formidable threats in the cybersecurity landscape, evolving with advancements in technology and tactics. Understanding how botnets are assembled, the vulnerabilities they exploit, and their multifaceted uses is crucial for developing effective defense strategies. By implementing comprehensive security measures, staying informed about the latest vulnerabilities, and fostering a culture of security awareness, individuals and organizations can significantly reduce their risk of falling victim to botnet-related attacks.
Frequently Asked Questions
What is the primary purpose of a botnet?
Botnets are primarily used to execute large-scale cyberattacks, such as DDoS attacks, data theft, spam distribution, and spreading malware. They provide cybercriminals with the ability to control numerous compromised devices to carry out these malicious activities efficiently.
How can organizations detect if their systems are part of a botnet?
Organizations can detect botnet infections by monitoring network traffic for unusual patterns, such as unexpected outbound connections, high volumes of traffic to unknown IP addresses, and irregular system behavior. Implementing advanced threat detection systems and conducting regular security audits can also help identify compromised devices.
Can botnets be completely eradicated once a device is infected?
While it's challenging to completely eradicate botnets, especially large and sophisticated ones, proactive measures can significantly reduce their impact. Regularly updating systems, using robust security solutions, and educating users can prevent infections. Infected devices should be isolated and cleaned using reputable antivirus and anti-malware tools to remove botnet components.
Tags: botnets, CVEs, cybersecurity, DDoS attacks, malware, network security, vulnerability exploitation, DNS amplification, NTP amplification, cyber threats