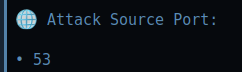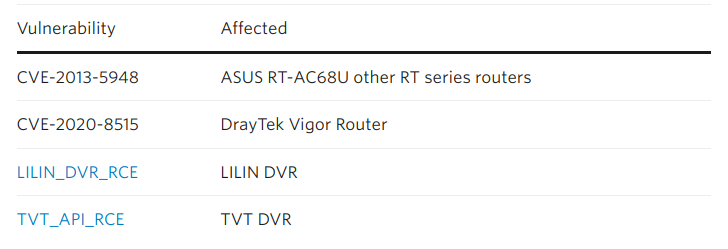
Botnets in Modern and CVE
OVERLOAD IP STRESSERSimulate real-world traffic and optimize your infrastructure with our advanced L4/L7 ip stresser booter. Table of Contents 1. What Are Botnets? 2. How Botnets Are Assembled Today * Exploiting Vulnerabilities (CVEs) * Phishing and Social Engineering * Malware Distribution 3. Common Vulnerabilities Used in Botnet Creation * Critical CVEs in Recent